How to Integrate Cloudflare with CSF Firewall
April 11th 2024 update: This article has evolved from “Replacing Cloudflare with CSF Firewall” to, “How to Integrate Cloudflare with CSF Firewall”.
Leveraging CSF for Enhanced Security on Cloudflare-enabled Websites
Over time, web infrastructure evolves, necessitating updates in our security and performance strategies. Notably, Bunny CDN served as a comprehensive caching solution for my blog up until 2022. But more recently, I’ve made a full switch to Cloudflare, even transferring the domain registration there. This guide is designed to provide insights and tips on harnessing CSF (Config Server Firewall) to bolster security, whether you’re using Cloudflare as a reverse proxy or not.
As web technologies and threats have advanced, so has the integration of security solutions like Cloudflare and CSF. Cloudflare for its CDN and security features, I’ve since explored combining it with robust server-side solutions for enhanced protection and performance. This guide reflects updates and practices beneficial for those using Cloudflare with CSF.
Background and Evolution
Cloudflare’s journey from a promising security solution to a staple in web infrastructure security has been remarkable. Following the Cloudbleed incident, the importance of proactive security measures became even more apparent. Despite challenges, the resilience and continuous improvement of Cloudflare’s services have solidified its place in my toolkit, complemented by CSF for a layered security approach.
Setting Up CSF with Cloudflare: A Guide
ConfigServer Security and Firewall (CSF) stands out as a versatile server firewall, offering a rich feature set while being accessible enough for quick installation and configuration. Whether you’re integrating CSF with a cPanel server or a standalone system, the process remains straightforward, enhancing your server’s security posture significantly.
Installation Steps
- Prepare for Installation:
- Navigate to
/usr/srcdirectory. - Download CSF installation package via
wget https://download.configserver.com/csf.tgz. - Extract the package and enter the directory.
- Navigate to
- Execute Installation:
- Choose the installation script based on your server setup (cPanel, DirectAdmin, etc.).
- Follow the script’s instructions to complete the installation.
- Configuration:
- Adjust key settings in
/etc/csf/csf.conf, focusing onTCP_IN,TCP_OUT, and other crucial firewall rules. - Transition CSF from TESTING mode to active by setting
TESTINGto"0"and restart CSF.
- Adjust key settings in
- Important: Whitelist Cloudflare IPs
- Visit: https://www.cloudflare.com/ips/. Paste the ips to
/etc/csf/csf.allow.
- Visit: https://www.cloudflare.com/ips/. Paste the ips to
Congratulations on installing CSF! This marks a significant step towards securing your local server environment.
Utilizing CSF: Tips and Tricks
CSF offers a plethora of command-line options to manage your firewall efficiently, from starting and stopping the firewall to updating rules and adding IP whitelists or blacklists. Familiarizing yourself with these commands can greatly enhance your server management experience.
Beyond Basic Firewall: CSF’s Advanced Features
- IP Block Lists: Leverage CSF’s ability to integrate with external IP blocklists for automatically updating firewall rules, enhancing protection against known threats.
- Port Flood Settings: Configure protection against SYN flood attacks, connection limits, and port flood attacks to mitigate DOS attempts.
- Cloudflare Integration: CSF can work in tandem with Cloudflare, providing a method to handle IP addresses that Cloudflare identifies as malicious.
- Connection and Process Tracking: Utilize CSF’s capabilities to monitor and block excessive connections, tracking suspicious processes, and automatically responding to potential threats.
If you would like me to create an article going over each of the CSF config settings, let me know. I’ve already written one for Cloudflare: Recommended Cloudflare Performance and Security Settings (Guide).
Conclusion
Integrating CSF with Cloudflare offers a robust security framework for your web infrastructure. While Cloudflare excels in CDN, SSL, and DDoS mitigation, CSF adds another layer of server-side security, from firewall rules to brute-force attack prevention. This synergy enhances your site’s security and maintains performance and reliability.
For those seeking alternatives or supplements to Cloudflare, CSF presents a viable option, promising a comprehensive security solution capable of addressing a wide array of threats. Moreover, considering additional security tools and practices can further fortify your web presence against the ever-evolving landscape of cyber threats.
Previous Article: Replacing Cloudflare with CSF Firewall (Archived)
March 8th, 2021 update: For the past year, this blog has been using Bunny CDN as a full-page caching solution. That said, I still use Cloudflare with other websites. I’m updating this guide with additional details and tips for using CSF (Config Server Firewall) to increase security with [or without] Cloudflare as a reverse proxy.
November 5th, 2018 update: I’ve updated this article (the install URL and other minor fixes/improvements). I replaced Cloudflare (check out: Cloudflare Argo) with KeyCDN + local firewall and server hardening for this blog as of June 2018. However, I do support clients who use Cloudflare and still highly recommend it.
2017 update: With the recent Cloudflare “Cloudbleed” data leak. You may be considering removing Cloudflare. This article (originally published three years ago) was updated and tested. I will be keeping Cloudflare. Please follow the URLs included at the end of this blog post for further details on this issue. A lot of Personally identifiable information (PII) is cached by Cloudflare, so it’s recommended that everyone take immediate action and change passwords on all sites that are running behind Cloudflare. It is always a good idea to change your passwords and change them often.
2016 update: Cloudflare has matured and grown a lot over the past three years. I highly recommend sticking with Cloudflare and using CSF to complement Cloudflare’s HTTP security. You’ll benefit from their global CDN, free SSL certificates, caching, and more. I’m currently using Cloudflare’s Pro plan and also full page caching along with CSF.
The founders of Cloudflare previously worked on the Project Honey Pot –> [ Update: Looks like Cloudflare removed mention of Project Honey Pot, which can be read here using the web archive ]. [Update 2: Mention of Project Honey Pot is back.] You can read more about installing CSF + Project Honey Pot below.
Cloudflare is extraordinary when set up correctly; however, it’s nice to have a free alternative for those who prefer to control server security without a reverse proxy.
As such, this is a quick guide on how to install and configure CSF (Config Server Firewall), its security plugin LFD (Login Failure Daemon), and how to set up IP filtering/blocking on your local server.
This guide applies to standalone CSF/LFD install and also cPanel + CSF/LFD install.
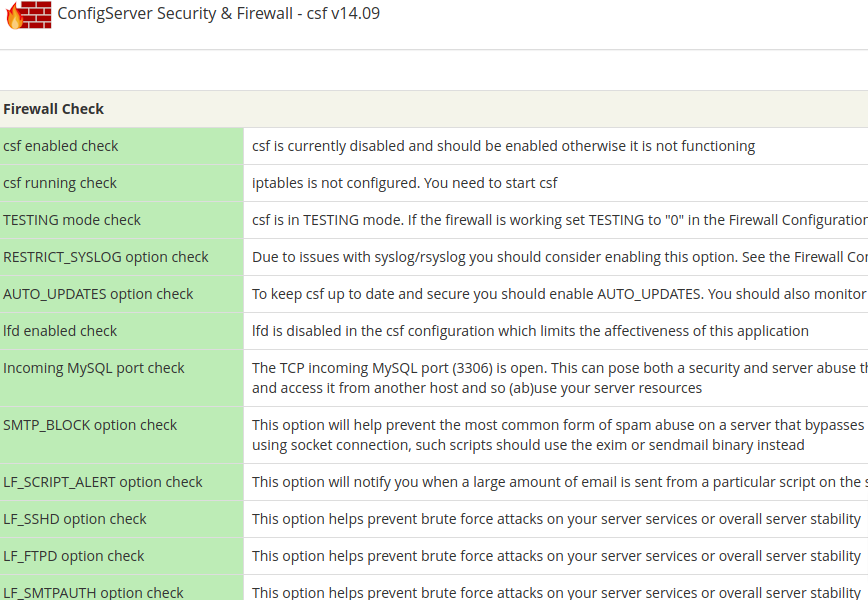
Installing CSF (Config Server Firewall)
CSF is a top-notch server firewall with many configuration options and is simple enough to install and configure that you can have it running in a few minutes.
It’s as easy as downloading the install file to your server then installing it. You can install CSF with cPanel/WHM integration or just regular installation.
The first few installation steps are the same whether it is a cPanel server or a non-cPanel server.
First, go to the directory /usr/src:
cd /usr/src
Next, use wget to retrieve CSF install code:
wget https://download.configserver.com/csf.tgz
Now decompress the CSF install files and change to the newly created csf directory:
tar zxf csf.tgz cd csf
Ok, here’s where the cPanel server vs. non-cPanel server install differs. If you’re using cPanel, then install with:
./install.cpanel.sh
If not, you should install with:
./install.sh
Also supported are install.cwp.sh, install.cyberpanel.sh, install.directadmin.sh, install.interworx.sh, and install.vesta.sh.
Read the output of the script as it installs. Once complete, you should see something similar to the following:
Don't forget to: 1. Configure the TCP_IN, TCP_OUT, UDP_IN and UDP_OUT options in the csf configuration to suite your server 2. Restart csf and lfd 3. Set TESTING to 0 once you're happy with the firewall Adding current SSH session IP address to the csf whitelist in csf.allow: Adding x.x.x.x to csf.allow only while in TESTING mode (not iptables ACCEPT) *WARNING* TESTING mode is enabled - do not forget to disable it in the configuration Installation Completed
Both CSF and LFD have been installed (in TESTING mode). To take CSF out of testing mode, edit the configuration with your favorite editor (or via the cPanel “Firewall Configuration” option):
vi /etc/csf/csf.conf
then change the following:
TESTING = "1"
to
TESTING = "0"
To restart CSF to enable:
csf -r
Congratulations! You’ve just installed CSF Firewall!
CSF command-line shortcuts
Here are some of the useful command-line shortcuts for working with CSF.
Option Meaning
-h, --help Show this message
-l, --status List/Show iptables configuration
-s, --start Start firewall rules
-f, --stop Flush/Stop firewall rules
-r, --restart Restart firewall rules
-a, --add ip Add an IP address to be whitelisted to /etc/csf.allow
-d, --deny ip Add an IP address to be blocked to /etc/csf.deny
-dr, --denyrm ip Remove and unblock an IP address in /etc/csf.deny
-c, --check Checks for updates to csf+lfd but does not perform an upgrade
-g, --grep ip Search the iptables rules for an IP match (incl. CIDR)
-t, --temp Displays the current list of temporary IP bans and their TTL
-tr, --temprm ip Remove an IP address from the temporary IP ban list
-td, --tempdeny ip ttl [-p port] [-d direction]
Add an IP address to the temporary IP ban list. ttl is how
long to blocks for in seconds. Optional port. Optional
direction of block can be one of in, out or inout. Default
is in
-tf, --tempf Flush all IP addresses from the temporary IP ban list
-u, --update Checks for updates to csf+lfd and performs an upgrade if
available
-x, --disable Disable csf and lfd
-e, --enable Enable csf and lfd if previously disabled
-v, --version Show csf version
For example, to block an IP, you can use: csf -d IPADDRESS. You can read about and fine-tune all settings by editing /etc/csf/csf.conf. For cPanel, you can edit from WHM under the “Plugins” area. Also see: http://configserver.com/cp/csf.html
Replace [or Complement] Cloudflare with CSF
Cloudflare is an American web infrastructure and website security company that provides content delivery network (CDN) services, DDoS mitigation, and distributed domain name server services. Cloudflare blocks IPs before they hit your website/server. To be clear, CSF cannot replace all of the features and many capabilities of Cloudflare. However, for many, CSF and a good CDN work great together for thousands of websites. For others, Cloudflare is a godsend. CSF and Cloudflare are similar in that they both use IP lists, similar to Project Honey Pot, the Web’s Largest Community Tracking Online Fraud Abuse project, and others similar organizations that provide regularly updated IP-blocklists.
CSF IP BLOCK Lists
This feature allows CSF to periodically download lists of IP addresses and CIDRs from published block or blacklists providers. The file that controls it is: /etc/csf/csf.blocklists. cPanel can also configure IP Blocklists using its UI.
Uncomment the line starting with the rule name to use it (read instructions at the top of the csf.blocklists file), then restart CSF.
The blocklists that can be enabled include those provided by spamhaus.org, dshield.org, torproject.org, cymru.com, projecthoneypot.org, ciarmy.com, maxmind.com, blocklist.de, stopforumspam.com, and greensnow.co.
IMPORTANT: Some of these lists can be very long – many thousands of IP addresses – and may cause severe network and performance issues if you try to load all the IPs. As such, it’s recommended that you set a value for the “MAX.” For example:
SPAMEDROP|86400|1000|http://www.spamhaus.org/drop/edrop.txt
Each URL gets scanned for an IPv4/CIDR address per line, then, if found, is blocked. (up to the max # of IPs you set).
Here’s what my file looks like (updated March 2021):
# Do not remove or change this line as it is a safeguard for the UI editor ############################################################################### # Copyright 2006-2018, Way to the Web Limited # URL: http://www.configserver.com # Email: sales@waytotheweb.com ############################################################################### # This file contains definitions to IP BLOCK lists. # # Uncomment the line starting with the rule name to use it, then restart csf # and then lfd # # Each block list must be listed on per line: as NAME|INTERVAL|MAX|URL # NAME : List name with all uppercase alphabetic characters with no # spaces and a maximum of 25 characters - this will be used as the # iptables chain name # INTERVAL: Refresh interval to download the list, must be a minimum of 3600 # seconds (an hour), but 86400 (a day) should be more than enough # MAX : This is the maximum number of IP addresses to use from the list, # a value of 0 means all IPs # URL : The URL to download the list from # # Note: Some of these lists may be very long and could cause serious network # and/or performance issues unless you are using LF_IPSET in csf, so setting a # value for the MAX field should be considered # # After making any changes to this file you must restart csf and then lfd # # If you want to redownload a blocklist you must first delete # /var/lib/csf/csf.block.NAME and then restart csf and then lfd # # Each URL is scanned for an IP/CIDR address per line and if found is blocked # # The downloaded list can be a zip file. The zip file MUST only contain a # single text file of a single IP/CIDR per line # # Note: CXS_ is a reserved prefix for the blocklist name and MUST NOT be used # Spamhaus Extended DROP List (EDROP) # Details: http://www.spamhaus.org/drop/ SPAMEDROP|86400|1000|http://www.spamhaus.org/drop/edrop.txt # DShield.org Recommended Block List # Details: https://dshield.org DSHIELD|86400|1000|https://www.dshield.org/block.txt # TOR Exit Nodes List # Set URLGET in csf.conf to use LWP as this list uses an SSL connection # Details: https://trac.torproject.org/projects/tor/wiki/doc/TorDNSExitList TOR|86400|1000|https://check.torproject.org/cgi-bin/TorBulkExitList.py?ip=1.2.3.4 # BOGON list # Details: http://www.team-cymru.org/Services/Bogons/ BOGON|86400|1000|http://www.cymru.com/Documents/bogon-bn-agg.txt # Project Honey Pot Directory of Dictionary Attacker IPs # Details: http://www.projecthoneypot.org HONEYPOT|86400|1000|https://www.projecthoneypot.org/list_of_ips.php?t=d&rss=1 # C.I. Army Malicious IP List # Details: http://www.ciarmy.com CIARMY|86400|1000|http://www.ciarmy.com/list/ci-badguys.txt # BruteForceBlocker IP List # Details: http://danger.rulez.sk/index.php/bruteforceblocker/ BFB|86400|1000|http://danger.rulez.sk/projects/bruteforceblocker/blist.php # Blocklist.de # Set URLGET in csf.conf to use LWP as this list uses an SSL connection # Details: https://www.blocklist.de # This first list only retrieves the IP addresses added in the last hour BDE|3600|5000|https://api.blocklist.de/getlast.php?time=3600 # This second list retrieves all the IP addresses added in the last 48 hours # and is usually a very large list (over 10000 entries), so be sure that you # have the resources available to use it #BDEALL|86400|0|http://lists.blocklist.de/lists/all.txt # GreenSnow Hack List # Details: https://greensnow.co GREENSNOW|86400|5000|https://blocklist.greensnow.co/greensnow.txt
CSF Port Flood Settings
Under this section of CSF, you’ll find SYN Flood Protection, Connection Limit Protection, Port Flood Protection, and Outgoing UDP Flood Protection. Here’s some suggested config:
SYNFLOOD = "0" SYNFLOOD_RATE = "100/s" SYNFLOOD_BURST = "150"
SYN flood configures iptables to offer some protection from TCP SYN packet DOS attempts. This option should ONLY be enabled if you know you are under a SYN flood attack as it will slow down all new connections from any IP address to the server if triggered.
CONNLIMIT = "22;5,80;20,443;20"
Connection Limit Protection configures iptables to offer more protection from DOS attacks against specific ports. It can also be used as a way to simply limit resource usage by IP address to specific server services. This option limits the number of concurrent new connections per IP address that can be made to specific ports.
PORTFLOOD = "22;tcp;5;300,80;tcp;20;5,443;tcp;20;5"
Port Flood Protection configures iptables to offer protection from DOS attacks against specific ports. This option limits the number of new connections per time interval that can be made to specific ports.
UDPFLOOD = "1" UDPFLOOD_LIMIT = "100/s" UDPFLOOD_BURST = "500"
Outgoing UDP Flood Protection limits outbound UDP packet floods. These typically originate from exploit scripts uploaded through vulnerable web scripts.
Read more about configuring these settings.
CSF Cloudflare integration
This section of /etc/csf/csf.conf provides interaction with the Cloudflare Firewall. Cloudflare is a reverse proxy, and as such, attacking IP addresses will appear to come from (or at least to iptables) Cloudflare’s own IPs. To solve this, read Restoring original visitor IPs: logging visitor IP addresses.
Cloudflare provides a Firewall API feature where rules can be added to block, challenge or whitelist IP addresses.
CSF Connection Tracking
Connection Tracking enables tracking of all connections from IP addresses to the server. If the total number of connections is greater than this value, then the offending IP address is blocked. This can be used to help prevent some types of DOS attack. Start less aggressive when setting this to avoid false positives. For a server that is prone to DOS attacks, this may be quite useful.
CT_LIMIT = "500" CT_INTERVAL = "30" CT_EMAIL_ALERT = "1"
CSF Process Tracking
Process Tracking enables tracking of user and nobody processes and examines them for suspicious executables or open network ports. If a suspicious process is found, an alert email is sent with relevant information. Allowing you to investigate the process.
PT_LIMIT = "300" PT_INTERVAL = "300"
CSF Port Scan Tracking
Port scan tracks port blocks logged by iptables to Syslog. If an IP address generates a port block that is logged more than PS_LIMIT within PS_INTERVAL seconds, the IP address will be blocked.
For example, port scan tracking can be used to block hackers attempting to access the standard SSH port if you have moved it to a port other than 22 and have removed 22 from the TCP_IN list so that connection attempts to the old port are being logged.
PS_INTERVAL = "300" PS_LIMIT = "10"
These are just a few of Config Server Firewall’s features.
Conclusion
Config Server Firewall is a free and mature firewall. In addition, firewall features CSF also includes other security features, such as brute-force attack protection, DDOS, port scanning abuse, and much more.
As a reminder, CSF does not improve your page load speed, lower server load, provide CDN, or many Cloudflare-specific features. Still, if for some reason you don’t want to use Cloudflare, then this is an alternative firewall for you. If you decide you are not using CDN for whatever reason, then you should also read my article: 25 Best CDN Providers.
For added security, you can also use additional tools or services, such as ModSecurity and Sucuri. Or, instead of CSF + LFD, you can use APF + BFD. There’s also bitninja.io, Imunify360 and others.