The Sony Hack: An Inside Job. Here’s why…
Update: Wiki page: https://en.wikipedia.org/wiki/Sony_Pictures_hack
From day one, as details leaked about stolen system administrator passwords, many of us knew that the Sony Hack had to have been an inside job. The simple reason is that system administrators setup notifications for both denied login attempts and more importantly, alerts for successful logins. These hackers reportedly stole a “System’s Administrator’s password” which gave them broad access to Sony’s computer systems. Yet, this high level breach went on for several weeks unnoticed by Sony’s IT?! What’s your take on the Sony Hack?
If hackers stole your admin credentials, would you know about it?
The above screen crop is a real alert I receive EVERY time I successfully log in to that server as admin (root). So yes, I’m alerting myself that I just logged in successfully. May seem strange to some, but this way, even if someone gains access to your admin credentials and are able to remotely use your PC or IP, you would still be notified by email and/or SMS. Imagine having lunch with your spouse or significant other, or just completing your workout at the gym and being alerted of a successful login using your password!
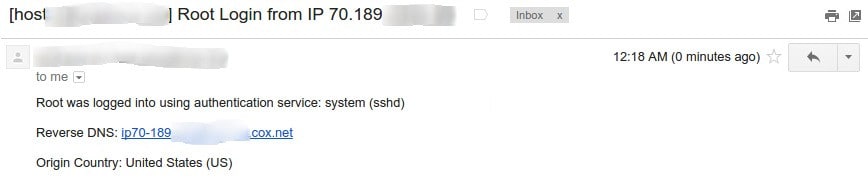
No doubt, Sony’s admins must have had this basic precaution in place. Thus, why I also believe this was, at least in part, an inside job! The above example was an alert from a cPanel based server. But using any Linux distro one can use free, paid or self coded solutions to accomplish this. For example, installing ConfigServer Security & Firewall and then configuring it’s LF_* security options. Thus, that’s what surprising about the Sony hack. Not that it happened, no, but rather that it was done using an admin’s credentials and yet went completely unnoticed… or, more likely, unreported.
“Against a sufficiently skilled, funded and motivated attacker, all networks are vulnerable.” so said security Guru Bruce Schneier. Therefore, we must plan for the worst and hope for the best. Here are some other precautions:
- Use difficult passwords (change them regularly).
- Use SSH keys for root access in lieu of passwords.
- Ensure multiple System Administrators don’t share the same accounts or passwords where possible.
- System Administrator access can be restricted to specific IPs and ports.
- Setup ongoing scanning for file uploads and changes to files/accounts which should also send out alerts.
- Avoid Microsoft Windows and server products when possible. Or know what’s involved in securing them.
- Add your suggestions in the comments…
Server security is very similar to home security, in that we spend time and money beefing up home security, yet we’ll still sleep with a baseball or cricket bat under our beds. (Or for many US States, a Pistol in the nightstand drawer.) In the same way, have a post-hack plan in place which starts with knowing when you are compromised!
Disclaimer: This article is in no way claiming that the Sony hack was limited to Linux systems. But instead focusing on general best practices related to this area of Linux web server administration. Sony and other large companies use (should use) enterprise level solutions to be notified immediately of breaches.