Linux Commands frequently used by Linux Sysadmins – Part 4
We are now up to part 4 of this five-part series entitled: Linux Commands frequently used by Linux Sysadmins. By the end of this series, we will cover at least 50 commands. Thus far, we have touched on around 60 commands often used by Linux Sysadmins and power users. Refer also to part 1, part 2, part 3, and part 5.
Let’s now look into another set of commands and command-line tools frequently used for filesystem management, security, permissions, networking, and other administrative tasks performed on Linux systems. After the final part of this series is posted, I will group related commands and interlink all five parts.
You’ll use these commands frequently whether you’re a Linux desktop power user
or an experienced Linux sysadmin. (Part 4 of 5)
The commands listed below are helpful for downloading remote files, using WHOIS from the command line, adding users, converting and copying files, etc. They are also helpful when attempting to fix an unbootable Linux system. Likewise, you can easily brick your system if you are unfamiliar with using some of these commands. I strongly recommend first testing some of these commands in your sandbox and home lab environments. See my home lab setup guide.
1. wget – retrieve files over HTTP, HTTPS, FTP, and FTPS.
wget is a command-line tool used for downloading files via HTTP, HTTPS, FTP, and FTPS. Because wget is command-line only, it can also be called up from scripts, cron jobs, and other non-GUI methods. The syntax for wget is as follows:
wget [option] [url]
So, for example, if you would like to download the official wget manual (a PDF file), you can use the following command:
# wget https://www.gnu.org/software/wget/manual/wget.pdf
What about CURL?
The most common wget alternative is curl. Curl supports more protocols, including FTPS, Gopher, HTTP, HTTPS, SCP, SFTP, TFTP, Telnet, DICT, LDAP, LDAPS, IMAP, POP3, SMTP, and URI. Curl is a highly flexible utility; you can, for example, use it to test a website’s TTFB (Time to First Byte) and a host of other uses.
Here’s an example of a curl command:
# curl -o /dev/null -w "Conn: %{time_connect} TTFB: %{time_starttransfer} Total: %{time_total} \n" https://linuxblog.io/
The above command runs a TTFB check on any website URL. Use man curl for an explanation of the above command arguments. Also, read Everything Curl.
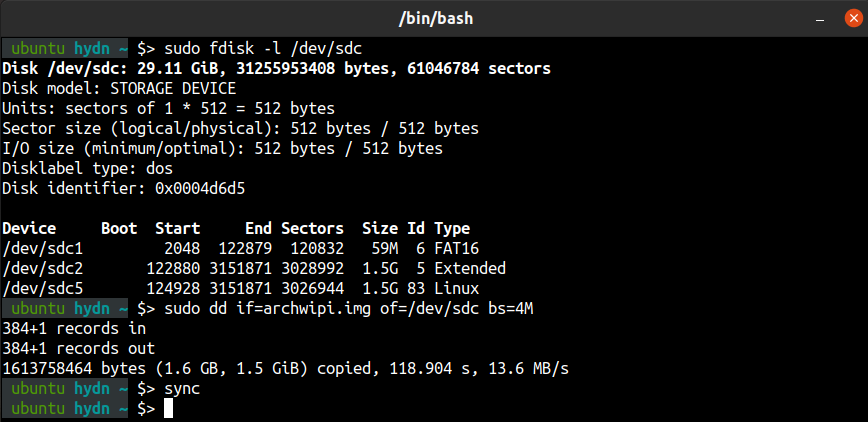
2. dd – convert and copy files.

Using dd – Always double-check that you’ve selected the correct device name.
Originally dd stood for “Copy and Convert”, but it was renamed because the C compiler already used cc. (Source: man dd from Unix-V7 on PDP-11) Many have wisely named dd as the “data destroyer” or “disk destroyer”.
dd is a very versatile utility available for Linux. The dd command-line utility’s primary purpose is to convert and copy files. One of the most popular uses of dd is to make USB boot drives from a .img or .iso file. For example, when first setting up the Raspberry Pi, you’ll need to copy the operating system to a USB stick (aka. thumb drive) for which you can use the dd command.
For example, here’s the command to write an .img or .iso to a USB stick or other bootable storage device:
$ sudo dd if=xbmc_new_os.img of=/dev/sdX bs=4M
Change /dev/sdX to the correct device name.
Warning: You will lose your data if you provide the wrong device name!
You can also reverse that command to backup the USB to your Linux system. However, if the USB is 32G and the storage used is only 8GB, then you won’t want to backup the entire 32GB device. You can use the following command and replace “XXXX” with the block count + 1 of the space used on the USB. You can find this using the fisk -l command, as discussed next.
$ sudo dd if=/dev/sdx of=new_os_backup.img bs=512 count=XXXX
Change /dev/sdX to the correct device name.
There are many other usages of the dd command. For example, the dd command can benchmark the performance of storage devices (i.e., SSD storage device), and can even benchmark your CPU.
Also read: Your Web Host Doesn’t Want You To Read This: Benchmark Your VPS.
Check out man dd.
3. fdisk – manipulate disk partition table.
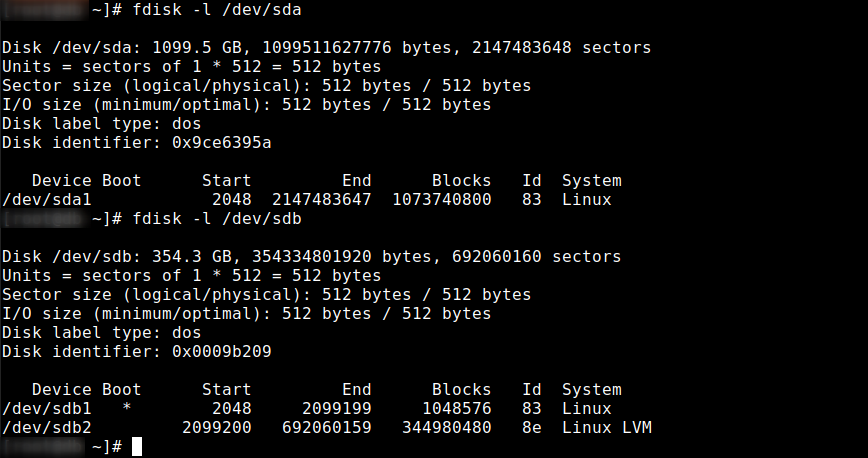
The fdisk utility is used to make changes to the partition table of storage devices. You can use the following command to list the partition table of all devices on a Linux system.
# fdisk -l
To display the partition for a specific device, including the device name. (see the example in the above screenshot):
# fdisk -l /dev/sda
Device: Shows the device name, followed by the partition number.
Boot: The Boot column shows that the first partition, /dev/sda1, has an asterisk (*), indicating that this partition contains the files required by the boot loader to boot the system.
Start and End: Shows the start and end of used blocks for each partition.
Blocks: shows the number of blocks allocated to the partition.
Id and System: Shows the partition type.
fdisk is a dialog-driven utility for the creation and manipulation of partition tables. Block devices can be divided into one or more logical disks called partitions. This division is recorded in the partition table, usually found in sector 0 of the disk. fdisk supports GPT, MBR, Sun, SGI, and BSD partition tables. A bad partition table can be fixed with fdisk.
To enter the fdisk command-driven utility, use the following command (replace sdX accordingly):
# fdisk /dev/sdX
Also, read Partitioning with fdisk.
Some related commands: parted, blkid, mkfs, fsck, etc.
4. whois – client for the whois directory service.
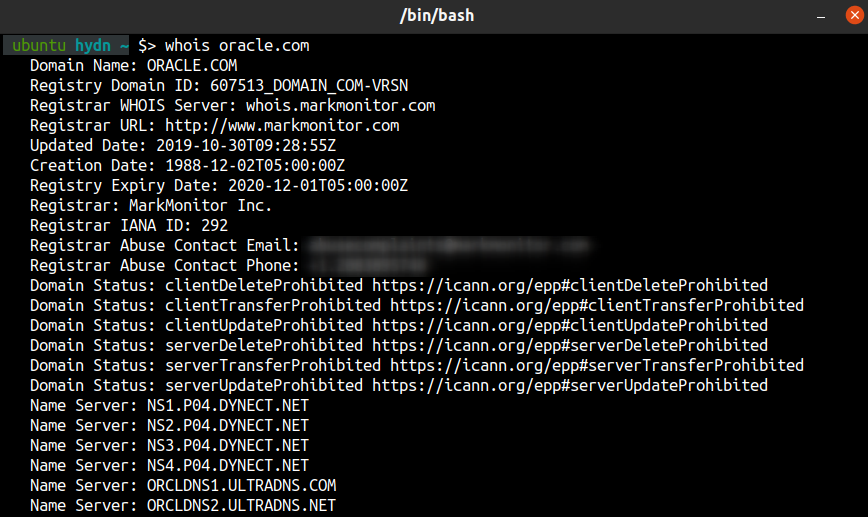
The whois command in Linux can be used to find out information about a domain, such as the domain owner, contact info, nameservers in use, etc. For example, to find out domain information for oracle.com, you can use the following command:
$ whois oracle.com
whois also queries whois.networksolutions.com for NIC handles or whois.arin.net for IPv4 addresses and network names.
5. nc – utility for TCP, UDP, or UNIX-domain sockets
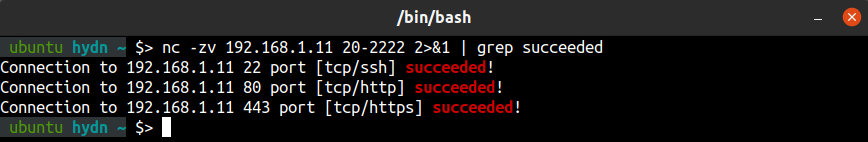
nc (netcat) is a convenient command-line networking utility. nc can be used for port scanning, port redirection, port listening, to open remote connections, to name just a few of its tricks.
To scan for open TCP port 22 on a remote machine with the IP address 192.168.1.11, you would use the following command:
$ nc -zv 192.168.1.11 22
To scan for open TCP port 22 and 80 on a remote machine with the IP address 192.168.1.11, you would use the following command:
$ nc -zv 192.168.1.11 22 80
To scan for open TCP ports on a remote machine with the IP address 192.168.1.11 in the port range of 20 to 8080, you would use the following command:
$ nc -zv 192.168.1.11 20-8080
Notice there’s a ton of connection refused for all the thousands of closed ports. If you would like to show only open ports you can use the following:
$ nc -zv 192.168.1.11 1-8080 2>&1 | grep succeeded
Useful Netcat cheatsheets and reading:
- Netcat Cheat Sheet – Source: sans.org
- Netcat Cheat Sheet – Source: Varonis.com
- en.wikipedia.org/wiki/Netcat#Examples
- Netcat Project homepage
- remember to use
man nc.
There are alternatives to netcat which you can read in my list of 60 Linux Networking commands and scripts.
6. umask – set file mode creation mask
umask (user file creation mask) is a command used to determine the settings of a mask which controls how file permissions are set for newly created files. It can also affect how file permissions are changed explicitly. This grouping of bits (mask) restricts how corresponding permissions are set for newly created files. Umask is used by open, mkdir, and other system calls to modify the permissions placed on newly created files or directories.
Learning umask:
- What Is Umask and How to Use it Effectively
- Umask – Configuring Default File / Directory Permissions
- Every Possible umask Mode
- Default umask Setting
7. chmod – change the access permissions of file system objects.
chmod (change mode) is the command and system call used to change the access permissions of Linux files and directories and to change special mode flags. The chmod request is filtered by umask. The command syntax goes like this:
chmod [options] mode[,mode] filename1 [filename2 ...]
To change the access permissions for a file, you can use the following:
$ chmod [mode] filename
To change the access permissions for a directory, you can use the following:
$ chmod [mode] directoryname
There is an easy way to set permissions by using octal modes. Read (r) permission is given the value 4, write (w) permission the value 2, and execute (x) permission the value 1. Like this:
r = 4
w = 2
x = 1
These values can be added together, for example:
1 = execute only
2 = write only
3 = write and execute (1+2)
4 = read-only
5 = read and execute (4+1)
6 = read and write (4+2)
7 = read and write and execute (4+2+1)
Access permissions can be set using three digits combinations. For example:
chmod 640 file1 = rw- r-- ---
chmod 754 file1 = rwx r-x r--
chmod 664 file1 = rw- rw- r--
Here’s an example command using octal numbers:
$ chmod 754 myfile
You can also set the exact permissions using symbolic modes. For example, this command also sets 754 permissions:
$ chmod u=rwx,g=rx,o=r myfile
Breakdown of command:
u - user
g - group
o - other
= - set the permissions exactly like this.
, - Commas separate the different classes of permissions (no spaces)
rwx = 7
rx = 5
r = 4
Useful chmod cheatsheets and reading:
- chmod codes cheat sheet.
- chmod cheat card.
- Changing File Permissions – Oracle.
- chmod permissions calculator.
8. chown – change file owner and group.chmod permissions calculator.
In Linux systems, every file is associated with group ownership and an owner. The chown (change owner) command is used to change ownership of file system files and directories. A non-root user cannot change ownership of a file, even if the user owns it. Only the root account can perform a change of ownership, while only a member of a group can change a file’s group ID to that group.
If an unprivileged user wishes to change the group membership of a file that they own, they can use the chgrp to do so.
The chown command syntax is as follows:
chown [OPTIONS] [USER][:GROUP] file[s]
[OPTIONS] = additional options. (optional)
[USER] = username or numeric user ID of the owner.
: = used when changing a group of a file.
[GROUP] = used when changing the group ownership of a file.(optional)
FILE = target file.
Here’s an example command:
$ chown -v SetUser:SetGroup /var/www/html/webfile
-v = verbose
Useful chown cheatsheets and reading:
9. chroot – run command or interactive shell with a special root directory.
The root, or “/”, is the mount point of the entire Linux file system, and any file or directory on the machine can be referenced back to this mount point. The chroot (change root) command is used to change the root mount point to a different location. For example:
# chroot /home/guest/jail
One of the most common reasons to make this change is to create a sandbox for either an application or a user. Once a new root is set using chroot, any references a user or application makes to “/” will then resolve to the new chroot directory. This is also a good way to restrict access to the system’s root and filesystem. A chrooted shell is also known as a jailed shell.
Chroot is also used when attempting live CD/USB recovery on a broken system which won’t boot.
Useful chroot cheatsheets and reading:
- Configuring and Using Chroot Jails.
- Basic Chroot – Ubuntu.
- Chroot – Gentoo wiki.
- How to Chroot in Rescue Mode.
- What chroot() is really for.
10. useradd – create a new user or update default new user information.
Adding and removing users is an essential Linux administration task. A new Linux server is often by default set up for access using only the root account. However, for performing many system administration tasks, it is better to add an unprivileged user.
For example, to add a new user named james, use this command:
# useradd -m james
The above command also automatically creates a group called james and makes it the default group for the user james. If you would like to set the default group to something else, use the -g option.
To set a password for the new user, use the following:
# passwd james
Related commands:
userdel – used to delete a user account and all related files.
usermod – used to modify or change any attributes of an existing user account.
sudo – For tasks requiring root privilege, you can use the sudo command. Basically, sudo allows you to run a command as another user, including root. After you add a new user, you may want to assign sudo privileges and delete users. – Also, see sudo.ws, and Arch Linux sudo wiki.
Bonus: Linux command-line extras
— cheat on your command line (Github):
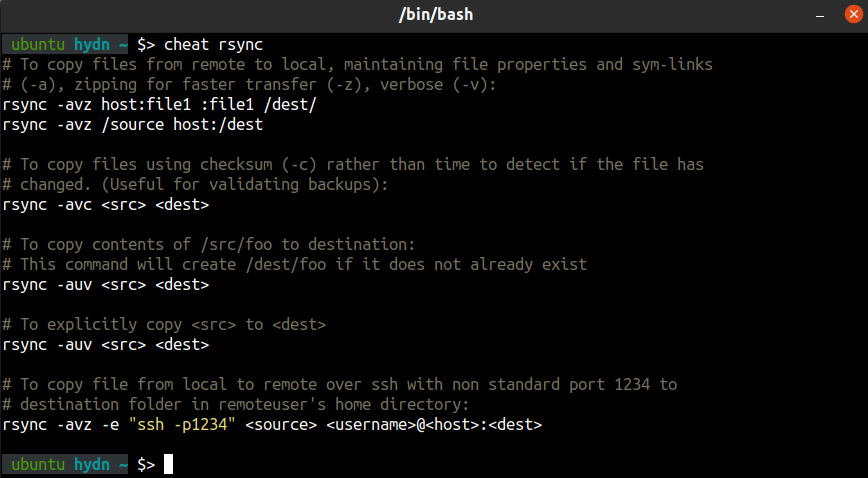
cheat allows you to create and view interactive cheatsheets on the command-line.
— The Linux Command Line – Second Internet Edition by William E. Shotts, Jr. – (PDF)
— Comprehensive Linux cheat sheet. (TXT)
— Command-line benchmark scripts.
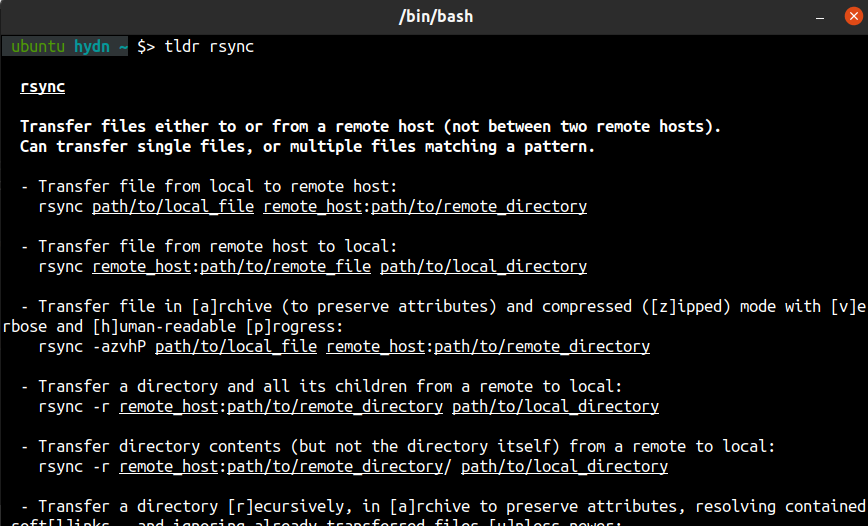
— tldr – Collaborative cheatsheets for console commands. – (Github)
That’s it for now! I hope you enjoyed part 4. Check back for part 5.
If you found this useful and you’d like to see additional series like this, please leave a note in the comments section below. Bookmark, share, subscribe and leave any comment or suggestions you may have.
< Previous – Linux Commands frequently used by Linux Sysadmins – Part 3
Next – Linux Commands frequently used by Linux Sysadmins – Part 5 >
That image perfectly sums up me using the dd command!
Question regarding wget vs curl. For just download a file, is there any benefit to one compared to the other? Maybe in terms of speed or security? I’ve always just used wget because it’s easier to remember.
That dd picture made me laugh. Data destoryer, huh? It’s a lifesaver when other tools fail. Like a knife, it can cut, but I use it carefully and it works well. I vaguely recall needing it to rescue/transfer data from a SysV machine to Solaris, dd was able to get around differences between tar and dump (sysV). Normal practice was to tar | network-glue | tar to transfer batches of files between machines, but the SvsV machine used dump, and the dump | net-glue | tar chain failed. dd | net-glue | dd worked on both machines, and my advisor was happy.
Data destoryer, huh? It’s a lifesaver when other tools fail. Like a knife, it can cut, but I use it carefully and it works well. I vaguely recall needing it to rescue/transfer data from a SysV machine to Solaris, dd was able to get around differences between tar and dump (sysV). Normal practice was to tar | network-glue | tar to transfer batches of files between machines, but the SvsV machine used dump, and the dump | net-glue | tar chain failed. dd | net-glue | dd worked on both machines, and my advisor was happy.
dd, whenfdiskis not enough.