SSH Security: Protecting Your Linux Server from Threats
SSH (Secure Shell) is our best friend when it comes to remote command line access to our servers. SSH (Secure Shell) is an essential tool for remote command-line access to servers. But to truly secure SSH you need to limit access to specific IP’s and follow a few other best practices. Leaving SSH open to the world (the default) is a huge security risk, it’s an open invite to brute force attacks and unauthorized logins.
In this article, we’ll cover how to limit SSH access to your Linux server by IP address. We’ll also cover some other SSH hardening tips that you may or may not already have in place.
The threats to our servers are constantly changing, so it’s important to harden our servers and be proactive with our server management. By following these tips, you can greatly reduce the chances of a security breach and ensure your servers continue to run smoothly.
SSH Security: Using the sshd_config File
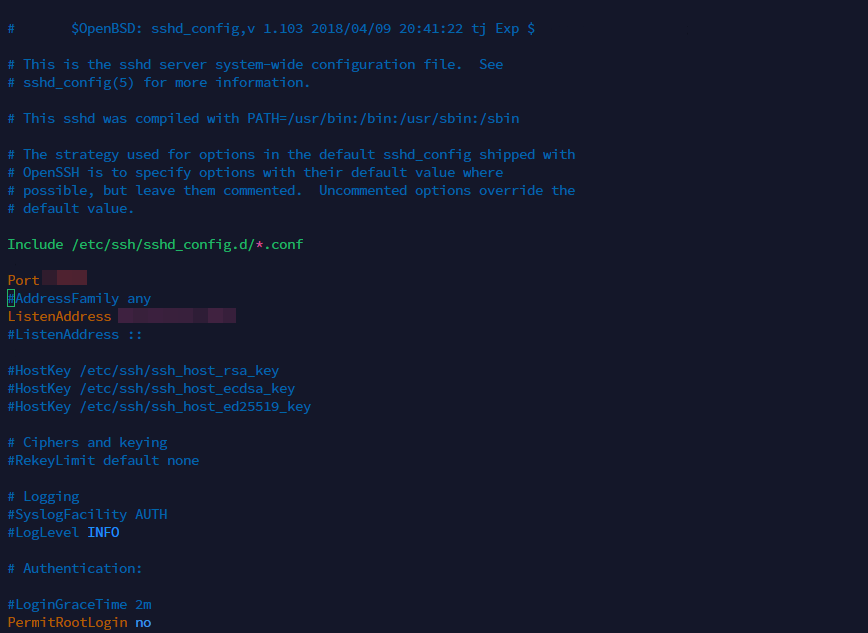
One of the easiest ways to restrict SSH access by IP address is to modify the sshd_config file, which controls SSH server settings.
Here’s how to do it:
Open the sshd_config file in a text editor:
vi /etc/ssh/sshd_config
Find the line that reads #PermitRootLogin yes and add the following line below it:
AllowUsers username@ip_address
Replace username with the username of the user you want to allow access and ip_address with the IP address of the computer, you want to allow access from. You can add multiple IP addresses separated by spaces.
Save and exit the file. Then restart the SSH service:
systemctl restart sshd
Now, only the specified user(s) will be able to access the server via SSH from the specified IP address(es).
SSH Security: Using TCP Wrappers
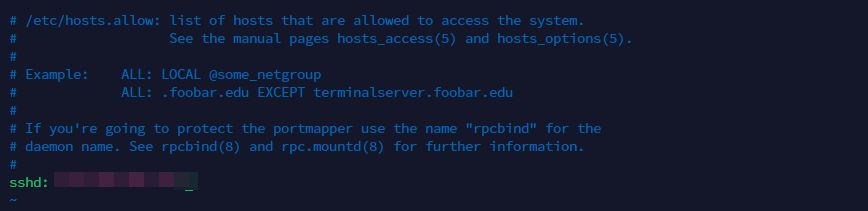
Another method to restrict SSH access by IP address is to use TCP wrappers. TCP wrappers are an access control mechanism that uses rules in the /etc/hosts.allow and /etc/hosts.deny files to allow or deny access to network services.
Here’s how to use TCP wrappers to restrict SSH access:
Open the /etc/hosts.allow file in a text editor:
vi /etc/hosts.allow
Add the following line to the file:
sshd: IP_address
Replace IP_address with the IP address of the computer you want to allow access from.
Then open the /etc/hosts.deny file in a text editor:
vi /etc/hosts.deny
Add the following line to the file:
sshd: ALL
This line will deny access to all other IP addresses.
Save and exit the files. Then restart the SSH service:
systemctl restart sshd
Now, only the specified IP address will be able to access the server via SSH.
SSH Security: Using Firewall Rules
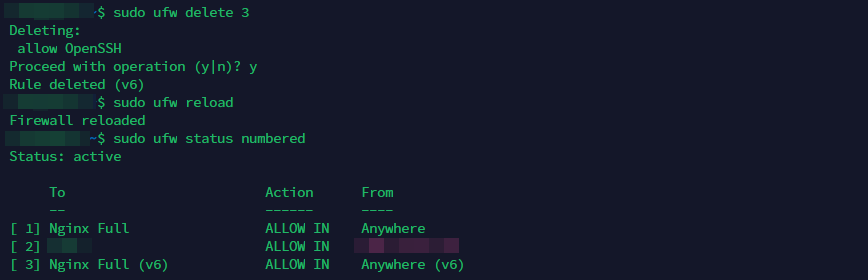
Finally, you can also use firewall rules to restrict SSH access by IP address.
Using iptables
Here’s how to use iptables, a popular firewall tool, to restrict SSH access:
Create a new iptables chain to allow SSH traffic from specific IP addresses:
iptables -N SSHALLOW iptables -A SSHALLOW -s IP_address -p tcp --dport ssh -j ACCEPT iptables -A SSHALLOW -j DROP
Replace “IP_address” with the IP address of the computer you want to allow access from.
Save the iptables rules:
service iptables save
To reload the iptables service after making changes to the firewall rules, you can use the following command:
sudo service iptables reload
This command will reload the iptables rules without interrupting any active SSH connections.
To learn more about using iptables, you can refer to the official documentation: https://netfilter.org/documentation/
Using ufw
If you are using the Uncomplicated Firewall (UFW) on your server, you can still use the same methods to restrict SSH access by IP address.
For example, to allow SSH access from a specific IP address, you can use the following command:
sudo ufw allow from [IP_address] to any port ssh
Replace [IP_address] with the IP address of the computer you want to allow access from.
Note: see below about using a non-standard port. Avoid using post 22 when possible.
To deny SSH access from all other IP addresses, you can use the following command:
sudo ufw default deny incoming
To reload the UFW after making changes to the firewall rules, you can use the following command:
sudo ufw reload
To learn more about using UFW, you can refer to the official documentation: https://help.ubuntu.com/community/UFW.
Using firewalld
If you are using firewalld as your firewall, you can still use the same methods to restrict SSH access by IP address.
For example, to allow SSH access from a specific IP address, you can use the following command:
sudo firewall-cmd --permanent --add-rich-rule='rule family="ipv4" source address="[IP_address]" port protocol="tcp" port="ssh" accept'
Replace [IP_address] with the IP address of the computer you want to allow access from.
To deny SSH access from all other IP addresses, you can use the following command:
sudo firewall-cmd --permanent --zone=public --remove-service=ssh sudo firewall-cmd --permanent --zone=public --add-rich-rule='rule family="ipv4" source address="! [IP_address]" service name="ssh" reject'
Replace [IP_address] with the IP address of the computer you want to allow access from.
To reload the firewalld service after making the changes, use the following command:
sudo firewall-cmd --reload
This command will reload the firewalld rules without interrupting any active SSH connections.
To learn more about using firewalld, you can refer to the official documentation: https://firewalld.org/documentation/.
SSH Security Hardening Best Practices
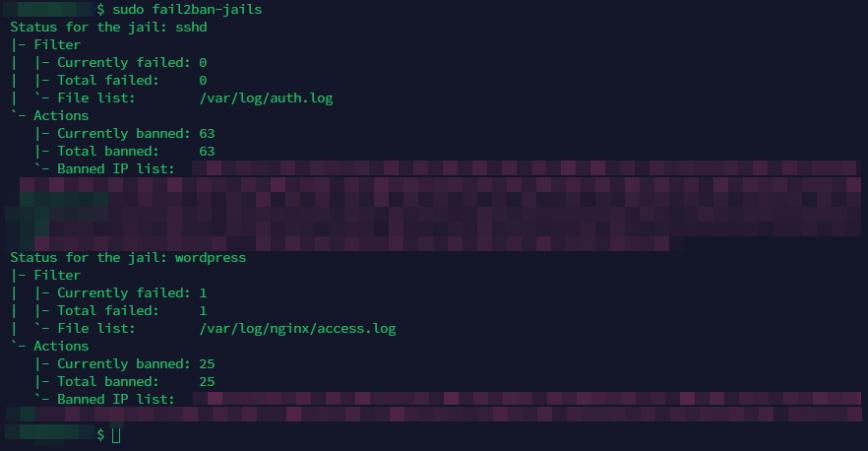
Showing all fail2ban jails at once. See here.
While restricting SSH access by IP address is an effective security measure, it’s not the only step you should take to secure your SSH server. Here are some other general SSH security hardening tips:
Use a non-standard port
By default, SSH listens on port 22. Attackers often scan for open ports and try to exploit vulnerabilities in SSH to gain unauthorized access. Changing the default port to a non-standard one can make it harder for attackers to find your SSH server. However, keep in mind that this is not a foolproof security measure and can still be bypassed by determined attackers.
To change the SSH port, edit the sshd_config file:
vi /etc/ssh/sshd_config
Find the line that reads “Port 22” and change it to a different port number. I wouldn’t recommend using port 2222 – also common. I would suggest some ports, but that would be counterproductive. Just ensure that any new port you choose is not already in use by another service or protocol. Remember to remove port 22 access in your firewall config.
It’s generally recommended to choose a port number within the range of 1024 to 65535, as ports between 1 and 1023 are well-known and often used by system services. It’s important to note that while using a non-standard SSH port can make it more difficult for attackers to find your server, it’s not a foolproof security measure and can still be bypassed by determined attackers.
Use SSH keys instead of passwords
Using SSH keys instead of passwords can further enhance the security of your SSH server. SSH keys are a form of public-key cryptography where a public key is used to encrypt data, and a private key is used to decrypt it. With SSH keys, there’s no need to transmit passwords over the network, which can be intercepted by attackers.
To use SSH keys, you need to generate a key pair on your local computer and copy the public key to the server. Then, you can configure the SSH server to only allow SSH connections from clients that present a valid private key. This can be done by modifying the sshd_config file:
vi /etc/ssh/sshd_config
Find the line that reads #PubkeyAuthentication yes and uncomment it:
PubkeyAuthentication yes
Save and exit the file, and then restart the SSH service:
systemctl restart sshd
Disable root login
By default, SSH allows root login, which can be a security risk. Attackers often try to guess the root password, and if successful, they can gain full access to your server. To mitigate this risk, it’s recommended to disable root login and use a regular user account instead.
To disable root login, edit the sshd_config file:
vi /etc/ssh/sshd_config
Find the line that reads #PermitRootLogin yes and change it to:
PermitRootLogin no
Save and exit the file, and then restart the SSH service:
systemctl restart sshd
Use Fail2ban
Fail2ban is a popular tool that scans log files and bans IP addresses that show malicious behavior, such as repeated failed login attempts. By using fail2ban, you can protect your SSH server from brute-force attacks and other types of attacks that rely on guessing passwords.
By default, fail2ban comes with a configuration file for SSH. However, you may need to adjust the settings to match your specific setup.
Please feel free to leave a comment in the section below if you are interested in a separate article that covers the installation and configuration of Fail2ban on servers.
Conclusion
In conclusion, securing your server with tools like Fail2ban and configuring your SSH server settings to limit access by IP address are essential steps to protect your system against brute-force attacks and other security threats. With the rise of cyberattacks at an alarming rate, it’s more important than ever to ensure that your server is secure and that you’re following best practices for server management.
Remember, server security is an ongoing process that requires continuous effort and attention. By making security a priority and taking steps to protect your server, you can reduce the risk of security breaches and ensure the continued operation of your system.
Great article, thanks! I would also add “port knocking” way here.
Thanks again, @vintka, for the great suggestion! Welcome to the forums
Let me add that info here in the article discussion as it is indeed via your suggestion.
Port knocking is a security technique used to protect servers from unauthorized access. It involves opening ports on demand by “knocking” on a predefined sequence of ports in a specific order.
Here’s how to set up port knocking on Ubuntu:
Install the Knockd daemon:
sudo apt update && sudo apt install knockdConfigure Knockd: Edit the Knockd configuration file:
sudo vi /etc/knockd.confDefine the port sequences and commands to execute. For example:
In this example:
openSSH: Opens the SSH port (replacexxxxwith your SSH port) when the sequence1000,2000,3000is knocked.closeSSH: Closes the SSH port when the reverse sequence3000,2000,1000is knocked.sudo systemctl enable knockd sudo systemctl start knockdThat’s it! Be sure to test your configuration thoroughly before deploying it in a production environment.
One of best ideas instead blacklisting or whitelisting some users or ip address is using a strong password for your user profile so it’s difficult to crack it and connect trough SSH.
Yes. Only if using keys isn’t an option. But even then, with strong passwords those attempting brute force should be blocked. I like using the honeypot project and also blocks by country using MaxMind.
Bookmarked! Great article, well explained